|
|
|
|
|
|
|
|
Previous Section | Next Section
All of the push applications share a common set of features and capabilities. This basic feature set includes the ability for the user to create an information profile (i.e., to define what information he or she would like to receive.) The content publisher has a similar capability to define which content to deliver to each end user. The client application must also be able to connect, notify the server of its presence, and receive the information for the user.
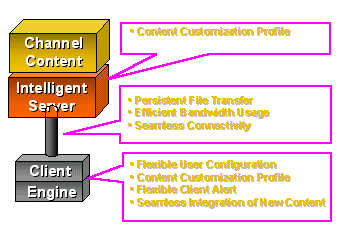
Figure7: Push Features
Most packaged push applications extend the common feature set considerably. A state-of-the-art content or file-type push system will provide the subscriber with control and messaging options, security, and intelligent use of bandwidth/connection. These push applications include features that are also important key components in ISV application development--features that embody the messaging, control, and transfer mechanisms. These components work in conjunction with client software to automate a poll of known sites and information.
This refers to the client's ability to easily connect to the Internet. Users connect to the Internet in many different ways, such as via an online service provider like AOL and CompuServe. They connect using analog and ISDN modems, or using direct connections via corporate LANs. The push client application must be able to recognize all of these connection types and be able to seamlessly establish a connection to the Internet. More sophisticated applications will have the ability to sniff out existing configurations without user input. If there is more that one possible connection method, the push application should provide a mechanism for the user to select or prioritize the connection method. "Seamless" means establishing the connection with minimal end user interaction or no user interaction in the case of unattended operation such as a midnight download. Unattended operation will become increasingly important for the delivery of larger data packages with multimedia content.
4.2 Flexible User Configuration
This refers to the user's ability to schedule connections and allocate resources. One key to making a push application successful is to ensure that the user is still in control of the PC, and can configure the interaction of that PC with the Internet to provide non-obtrusive collection of information. The publisher or push vendor should supply the user with the ability to schedule the connection time, length, etc. In addition, the client should control what type of information to transfer, the size, where to store it, what to save, what to replace, etc. This feature is becoming increasingly important as recent press reports claim that the population of remote users without permanent connections is increasing in relation to desktop users.
4.3 Content Customization Profile
This refers to the subscriber's customization of his or her information profile and to the publisher's customization of both the content and the delivery parameters of the content.
Subscriber: The ability to select topics and sub topics from a channel publisher or content provider which are used to select and filter information for download.
Publisher: The ability to divide content into categories that will appeal to users, as well as to specify when, how, and for how long content is displayed. Includes the ability to target that information to a specific audience based on user profile information. (Push technology is a wonderful opportunity for publishers because it allows the publisher to accurately target the audience most likely to provide a return on its investment, either through advertising or through the sale of content.)
This refers to the ability to stop a data transfer at any point and to continue from that point when the connection becomes available again. This feature is most important when delivering large files. Because push applications excel at the transfer of rich multimedia, many are designed to go one step further than the standard information transfer mechanisms such as ftp or http. Those with proprietary transfer capabilities or close client/server interactions can provide the capability to save file transfer information on the client if the connection is lost. On the next poll for information from the server, the information transfer can pick up where it left off.
CLIENT CENTRIC: The client's maximizes the use of available bandwidth via the use of idle time downloading. BackWeb* has a technology called Polite Agent(tm) that can use idle time to download files from the server.
SERVER CENTRIC: The server specializes in succinct and specialized information transfers, such as Minimal Updates: the ability to send minimal data by re-using components that already exist on the client. One vendor (Marimba*) uses MD5 (Message Digest 5) checksum as a distinct signature for a file. Thus even if two files are named differently, their sameness will be noted and the component will be reused as opposed to downloading an additional copy.
4.6 Seamless Integration of New Content
This refers to the application's ability to transfer and integrate new or updated content with existing content. This replaces the user's ability to download a file and install it. These applications automatically determine what information, or what portion of the information, to download, where to store it, and what to replace. Some can actually execute the replacement data. Pointcast* is the perfect example of an application based on this ability.
4.7 Flexible Client Alert Capability
This refers to the client's ability to notify a user that new information exists or has arrived. This notification can range from simple dialog boxes to task bar icons to animations with sound and video. The type of alert depends on the type and importance of the information being transferred. (If the client alert is not configured properly to the type of data and user preferences, the user is apt to unsubscribe.)
This refers to the ability to ensure asset integrity and authorship, and that assets are only received by the intended client (or become unusable). Also must ensure that the assets that are invoked on the end user's system are secure within that system, like JAVA*.
This refers to the IP protocol family, upon which the Internet is based. The two main protocol transports within that family are TCP and UDP. Although TCP is reliable, it's not timely because its main focus is on making sure packets arrive at their destination. It will degrade performance to achieve that goal. UDP cares less about reliability and more about moving packets through a network as quickly as possible. This means that packets may be lost in the process of achieving maximum throughput and it is the application's responsibility to make the transport reliable. Many corporate firewalls are configured to block incoming UDP packets and incoming TCP/IP connections.
Most applications use the HTTP (TCP Port 80) protocol. The advantages of HTTP is that it is able to flow through firewalls (using outgoing connections) and the transmission is reliable based on TCP/IP. Browsers are based on HTTP. The disadvantage is that features to make applications "real-time" are not easily created.
Some push vendors have developed proprietary protocols that use the UDP transport. This means that these applications have difficulty with network environments secured with firewalls, and require special setup--if they can be used at all. (This depends on environment security requirements.) The advantage of proprietary protocols is that they allow some key features to be used--persistent file transfer, efficient bandwidth utilization techniques, etc.--that are much more difficult to implement via HTTP (at this time).
Back to Cookbooks | Back to Top
Previous Section | Next Section
* Other brands and names are the property of their respective owners